MattGPT
I am able to run a local GPT platform based on this software. I have also added it to my SSO and I think that's pretty neat. This means if you want access, you can ask me for it.
Here's my Docker Compose and Authelia config.
docker-compose.yaml
services:
ollama:
image: ghcr.io/open-webui/open-webui:ollama
container_name: mattgpt
volumes:
- ollama:/root/.ollama
- open-webui:/app/backend/data
environment:
WEBUI_URL: 'https://gpt.domain.com'
ENABLE_OAUTH_SIGNUP: 'true'
OAUTH_MERGE_ACCOUNTS_BY_EMAIL: 'true'
OAUTH_CLIENT_ID: 'gpt-oidc'
OAUTH_CLIENT_SECRET: 'makeupanicelongstringofletters'
OPENID_PROVIDER_URL: 'https://auth.domain.com/.well-known/openid-configuration'
OAUTH_PROVIDER_NAME: 'Authelia'
OAUTH_SCOPES: 'openid email profile groups'
ENABLE_OAUTH_ROLE_MANAGEMENT: 'true'
OAUTH_ALLOWED_ROLES: 'gpt-access,gpt-admin'
OAUTH_ADMIN_ROLES: 'gpt-admin'
OAUTH_ROLES_CLAIM: 'groups'
ports:
- 8080:8080
restart: always
network_mode: bridge
deploy:
resources:
reservations:
devices:
- driver: nvidia
count: 2
capabilities: [gpu]
volumes:
ollama:
driver: local # Define the driver and options under the volume name
driver_opts:
type: none
device: ./ollama
o: bind
open-webui:
driver: local # Define the driver and options under the volume name
driver_opts:
type: none
device: ./open-webui
o: bind
authelia-configuration.yml
For a functioning Authelia instance, pertinent configurations included
access_control:
rules:
# MattGPT access
- domain: gpt.domain.com
policy: one_factor
subject:
- "group:gpt-access"
- "group:gpt-admin"
identity_providers:
oidc:
clients:
- id: gpt-oidc
client_id: gpt-oidc
client_name: "gpt-oidc"
description: gpt-oidc
secret: 'makeupanicelongstringofletters'
sector_identifier: 'auth.domain.com'
public: false
response_types:
- 'code'
authorization_policy: one_factor
consent_mode: implicit
#pre_configured_consent_duration: 6m
audience: []
scopes:
- openid
- groups
- email
- profile
redirect_uris:
- https://gpt.domain.com
- https://gpt.domain.com/oauth/oidc/callback
access_token_signed_response_alg: 'none'
userinfo_signing_algorithm: none
token_endpoint_auth_method: 'client_secret_basic'
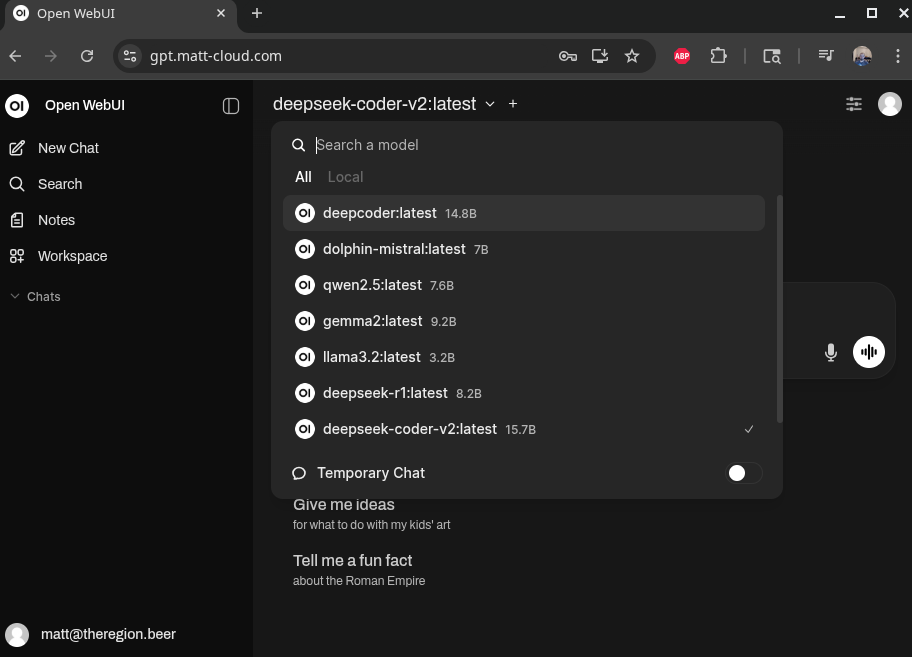
Sample Screenshot.
No Comments